Prevent your organisation from becoming the next victim.
Crypto-ransomware is quickly becoming one of the most prevalent types of cybercrime in the world.
These attacks offer an attractive set of advantages to cybercriminals. They are easy to automate, highly lucrative, and hard to detect using traditional cybersecurity systems. As a result, there has been a 139% year-over-year increase in ransomware attacks since 2019.
There are hundreds of different forms of crypto-ransomware, and each one operates slightly differently. What they share in common is the ability to defraud organisations of their critical data.
What is Crypto-Ransomware?
Crypto-ransomware is a kind of malware that encrypts victims’ files. Once inserted on a network, it looks for critical data files of many different types and gains ownership over them. Once it reaches a certain threshold, the malware activates and encrypts all of the files it has access to.
These encrypted files are unreadable, unusable, and largely inaccessible. At this point, the people behind the attack demand a ransom in exchange for the key that can decrypt the victim’s files. These ransoms can cost anywhere from a few hundred to millions of dollars. In 2020, ransomware victims paid an average of $312,493 USD to cybercriminals. Cybercriminals use a combination of sophisticated technology and psychological manipulation to convince victims to pay. Once the payment is made, there is no guarantee that the criminals will keep their word and provide the necessary decryption key – or refrain from attacking again in the future.
How Does Crypto-Ransomware Work?
In order to infect a network device, cybercriminals first need to get malicious software onto the network. Email phishing is one of the most popular methods of infiltrating a network. This is when cyber criminals attach malicious files or links to emails impersonating trustworthy figures – like financial institutions, coworkers, or even friends and family members.
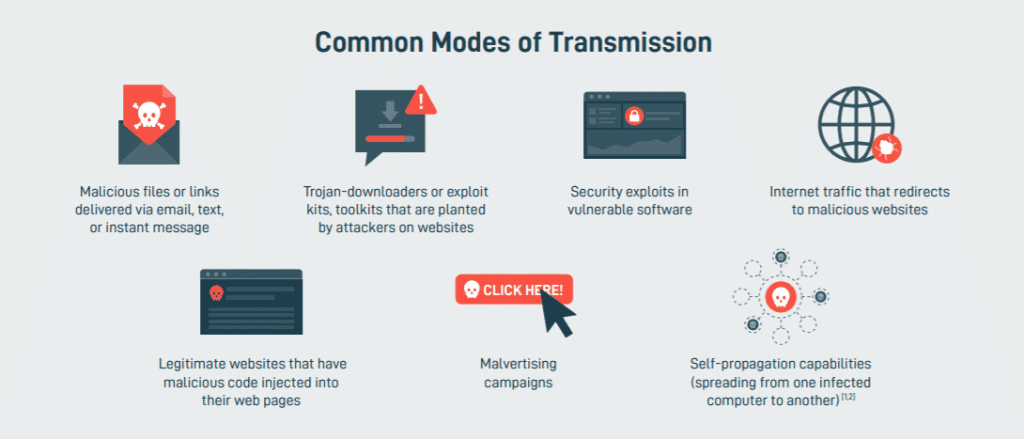
Other common modes of transmission include:
- Exploit kits hosted on spoof websites designed to impersonate real ones.
- Security exploits in old software or obsolete operating systems.
- Compromised network infrastructure that redirects Internet traffic to malicious websites.
- Legitimate websites that have malicious code injected into their web pages.
- Malicious advertisements.
- Self-propagation from an infected device on the same network.
Ransomware doesn’t activate immediately after an employee mistakenly downloads a malicious file. Instead, it works slowly, gaining permissions access to small bits of data on its local network at a snail’s pace. This is why traditional cybersecurity solutions fail to see ransomware in action until it is too late. It’s easy for security software to prevent an unknown application from obtaining permission to encrypt thousands of files at once. It’s much harder to notice permissions changing for just a handful of files per day. In a few weeks’ time, the malicious software will be ready to trigger.
Once the encryption triggers, victims lose access to their critical data and applications. In many cases victims cannot even access their computers at all. Sophisticated ransomware variants can encrypt the contents of networked drives, external storage devices, and even cloud storage deployments. Once the encryption occurs, all of that data is rendered unusable.
Top 5 Sectors Targeted by Ransomware in Australia
Anyone that stores information digitally is a potential ransomware target. Cybercriminals understand that certain industry sectors tend to value their data more than others and tailor their efforts to target these types of organisations. According to the Australian Cyber Security Centre, in 2020, 58% of all ransomware attacks targeted these five industries:
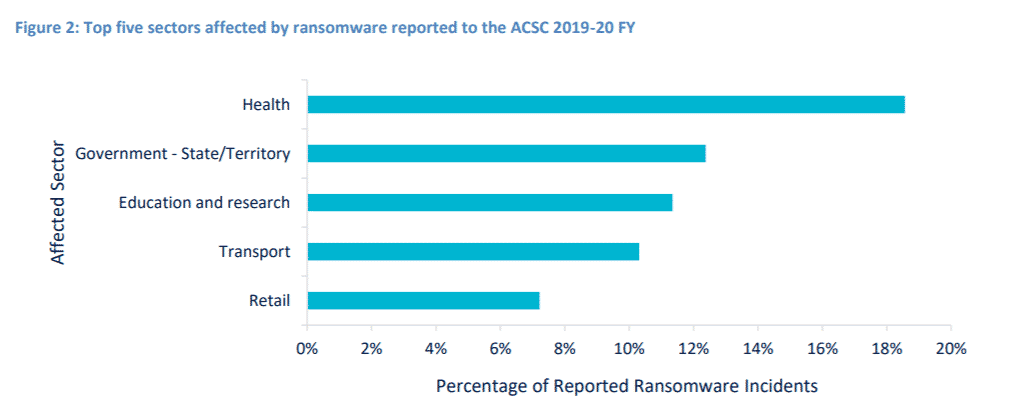
- Healthcare organizations reported 18%.
- Government organizations reported 12%.
- Education and Research organizations reported 11%.
- Transport organizations reported 10%.
- Retail companies reported 7%.
How to Identify a Ransomware Attack
Although ransomware attacks are incredibly difficult to spot during their early phases, it’s not impossible. Vigilant, well-informed employees who know how to spot early signs of ransomware infection may be able to save the company hundreds of thousands of dollars in costs.
- Unusual file name changes are among the earliest potential indicators of ransomware infiltration. This is especially true if there are no logs indicating who changed the file name in question. If employees notice unreported changes being made to sensitive files, reporting to a security professional will help determine whether it’s a false alarm or not.
- Lockout screens are a mid-stage indicator of ransomware infection. At this point, the malicious software has already expanded throughout the network and encountered sensitive databases that require authentication to access.
- If the software fails to authenticate its credentials to an application, it may lock users out of the application and require an IT administrator to unlock it. If applications are mysteriously locking themselves without a clear cause, ransomware may be behind the unusual behaviour.
- The final stage of the attack is encryption and ransom note. At this point, you are locked out of your data entirely. Your business will suffer costly downtime – $274,200 USD on average – and have to replace the data if lost. If you have timely and accurate backups readily available beforehand, you will be able to respond effectively.
How to Respond to Crypto-Ransomware When it Strikes

Whether responding to an early-stage infection or business-wide ransomware shut down, every second counts. The best way to defeat ransomware is by restoring data from uninfected backups. The process of safely accessing and recovering those backups is key.
Once you suspect a ransomware attack, perform the following:
- Scan networks to confirm the attack and identify its trajectory.
- Isolate infected devices immediately.
- Secure backup data and systems by taking them offline.
- Ensure your backups are free of malware.
- Collect portions of ransomed data if possible.
- Change all account passwords for Internet-enabled services and applications after removing them from the network.
- Delete Registry values and files. This will stop ransomware applications from loading.
- Contact law enforcement.
If your organisation has a multi-layered security solution that involves active network monitoring, you will be able to scan for malware and process alerts in real-time. This can help you take preventative actions like restricting unauthorized accounts, patching obsolete software, and implementing multi-factor authentication on endpoints like desktops, laptops, and tablets.
Datto Ransomware Detection and All-in-One Business Continuity Protection
Datto uses patent-pending technology to monitor systems for crypto-ransomware in real-time. It alerts managed service providers the moment that ransomware begins encrypting files, making it possible for users to save their data and keep their business running.
Datto’s RMM Ransomware Detection automatically isolates the infected device from the network, minimising the extent of damage done. This helps contain the spread of ransomware and ensures that Datto’s SIRIS technology can begin restoring critical business systems from a secure, cloud-based repository immediately.
Get in touch with the MSP team at SMB Solutions today to learn more about how we can help protect your organisation from the threat of crypto-ransomware.